
- SAP Community
- Products and Technology
- Technology
- Technology Blogs by SAP
- Light introduction to Network Protocols
Technology Blogs by SAP
Learn how to extend and personalize SAP applications. Follow the SAP technology blog for insights into SAP BTP, ABAP, SAP Analytics Cloud, SAP HANA, and more.
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
former_member23
Explorer
Options
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
02-18-2020
12:23 PM
You can't build a system without some idea of what you want to build
Obvious, ha? strangely enough, it is not.
This is one of a few technical posts I am writing about distributed systems,cryptography and Blockchain.
In this post I will oversimplify a few concepts around networked applications in general, messaging techniques and share some code snippets along the way.
Protocols
Distributed systems are interesting. for example there are multiple devices are connected
and have to exchange information in someway.
Programs and applications have to run on each device and cooperate in
someway to get some task done.
A complex problem usually split into smaller parts that have a
defined function and are able to communicate with each other through a well defined messages.
These messages are the protocol.
Protocols are important because they encapsulate a lot of complexity so
that application developers focus on solving business problem or improving the user interface.
OSI Layers
Although it has never been properly implemented, the OSI Layers have a lot of influence when talking about distributed systems.
| Application Layer |
| Presentation Layer |
| Session Layer |
| Transport Layer |
| Network Layer |
| Data link Layer |
| Physical Layer |
read more https://en.wikipedia.org/wiki/OSI_model.
- A repeater operates at the physical level and copies information from one subnet to the other.
- A bridge operates at the data link layer level and copies frames between networks.
- A router operates on the network level, not only moves information between networks but decides on the route.
Packet Encapsulation
The communication between the layers are done by sending packets from one layer to the other, each layer has administrative data that it has to keep about its layer. It adds this header information to the packet it receives as it moves along to the next layer.
Connection Modes
Connection Oriented
A single full duplex connection is established for the session as we will see later.Think about a phone call and TCP.
Connectionless
Messages are sent independent of each other. Think about mail and UDP.
Communication Models
Message Passing
Message passing is a primitive mechanism for distributed systems communication.
Simply setup a connection and pump some data in there. The full torrent client code can be found here.
Lets dig here more since similar techniques are used in open blockchains.
func NewHandshake(infoHash [20]byte, peerID []byte) *Handshake {
handShake := Handshake{}
handShake.Pstrlen = byte(19)
handShake.Pstr = "BitTorrent protocol"
handShake.Reserved = [8]byte{0, 0, 0, 0, 0, 0, 0, 0}
copy(handShake.InfoHash[:], infoHash[:])
copy(handShake.PeerId[:], peerID[:])
return &handShake
}Here is a hex of the handshake message of the torrent protocol
13426974546f7272656e742070726f746f636f6c0000000000000000e2467cbf021192c241367b892230dc1e05c0580e1400000000000000000000000000000000000000func peerConnect(){
handShake := message.NewHandshake(t.TorrentFile.InfoHash, PeerId)
handshakeBytes := handShake.Serialize()
c, err := net.DialTimeout("tcp4",peer.GetAddr().String(),3*time.Second)
_, err := c.Conn.Write(handShakeBytes)
}here is the over wire bytes
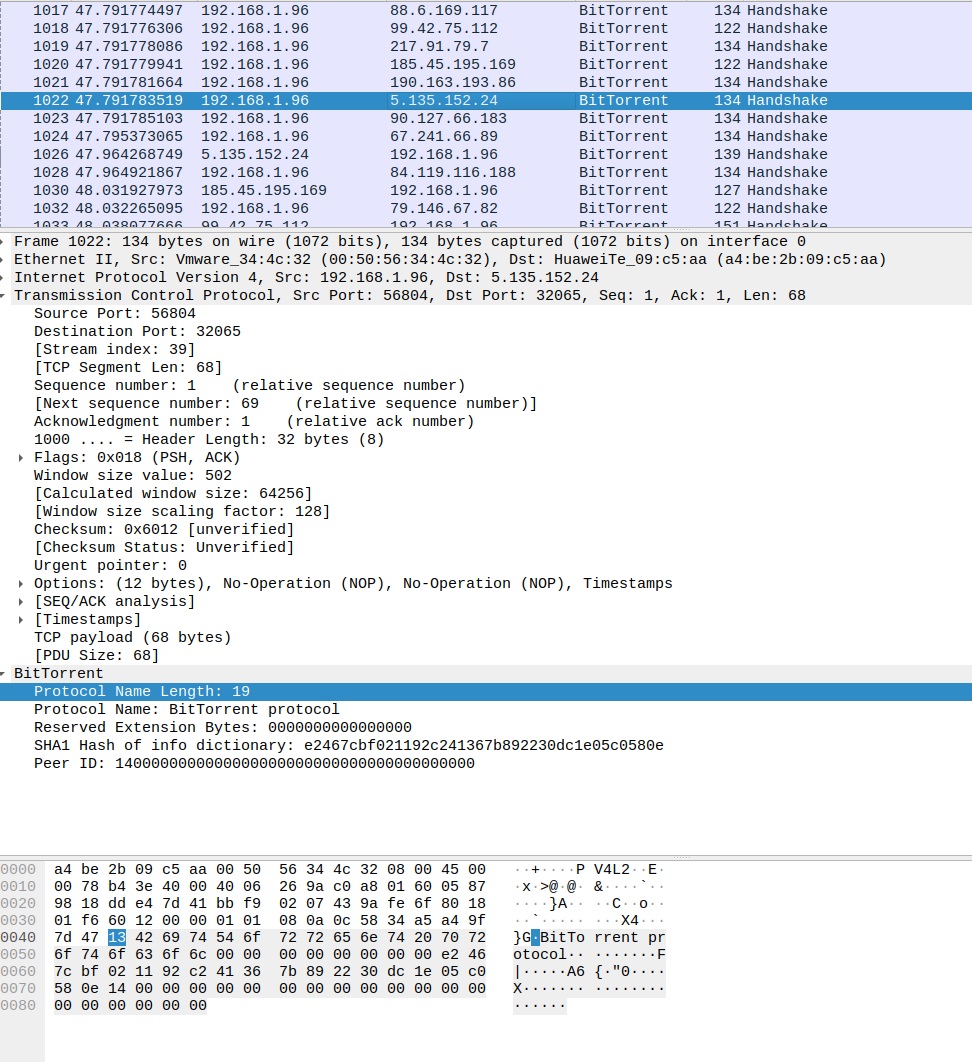
If the remote peers understand the protocol, they will respond according to the specification.In this case its another handshake message followed by a bitfield of the available pieces they have.

Remote Procedural Calls
This is when a computer or a device causes a procedure or subroutine to execute on another address space, machine.
Conclusion
You learnt about some fundamental terms and techniques used in protocol implementations and peer to peer to messaging.
If you wondering how it ties up to blockchain you will have to wait until the blog series complete.
You can find more at https://youssefnotes.net.
Disclaimer
The use Torrent protocol is not illegal.
Downloading copyrighted material is illegal.
Don't use it to download illegal/copyrighted material.
This guide and the accompanied code snippets are for educational purposes only.
- SAP Managed Tags:
- Blockchain
Labels:
You must be a registered user to add a comment. If you've already registered, sign in. Otherwise, register and sign in.
Labels in this area
-
ABAP CDS Views - CDC (Change Data Capture)
2 -
AI
1 -
Analyze Workload Data
1 -
BTP
1 -
Business and IT Integration
2 -
Business application stu
1 -
Business Technology Platform
1 -
Business Trends
1,658 -
Business Trends
93 -
CAP
1 -
cf
1 -
Cloud Foundry
1 -
Confluent
1 -
Customer COE Basics and Fundamentals
1 -
Customer COE Latest and Greatest
3 -
Customer Data Browser app
1 -
Data Analysis Tool
1 -
data migration
1 -
data transfer
1 -
Datasphere
2 -
Event Information
1,400 -
Event Information
67 -
Expert
1 -
Expert Insights
177 -
Expert Insights
301 -
General
1 -
Google cloud
1 -
Google Next'24
1 -
GraphQL
1 -
Kafka
1 -
Life at SAP
780 -
Life at SAP
13 -
Migrate your Data App
1 -
MTA
1 -
Network Performance Analysis
1 -
NodeJS
1 -
PDF
1 -
POC
1 -
Product Updates
4,577 -
Product Updates
346 -
Replication Flow
1 -
REST API
1 -
RisewithSAP
1 -
SAP BTP
1 -
SAP BTP Cloud Foundry
1 -
SAP Cloud ALM
1 -
SAP Cloud Application Programming Model
1 -
SAP Datasphere
2 -
SAP S4HANA Cloud
1 -
SAP S4HANA Migration Cockpit
1 -
Technology Updates
6,873 -
Technology Updates
430 -
Workload Fluctuations
1
Related Content
- SAP BW/4 - revamp and true to the line 2024 in Technology Blogs by Members
- Integrating Smart contracts with SAPUI5 in Technology Blogs by Members
- IoT - Ultimate Data Cyber Security - with Enterprise Blockchain and SAP BTP 🚀 in Technology Blogs by Members
- ABAP Cloud Developer Trial 2022 Available Now in Technology Blogs by SAP
- Explore Business Continuity Options for SAP workload using AWS Elastic DisasterRecoveryService (DRS) in Technology Blogs by Members
Top kudoed authors
| User | Count |
|---|---|
| 29 | |
| 18 | |
| 14 | |
| 13 | |
| 11 | |
| 9 | |
| 8 | |
| 8 | |
| 8 | |
| 7 |